
- Home
- Managed Services
- Cyber Security
- Blog
- About Us

We, Global Cyber Tech, simplify your IT problems
Call for a free support. +1 -8273-456-478Platform Partnership
- Pages
- Who We Help
- Shop
- Contact Us



VPN Background
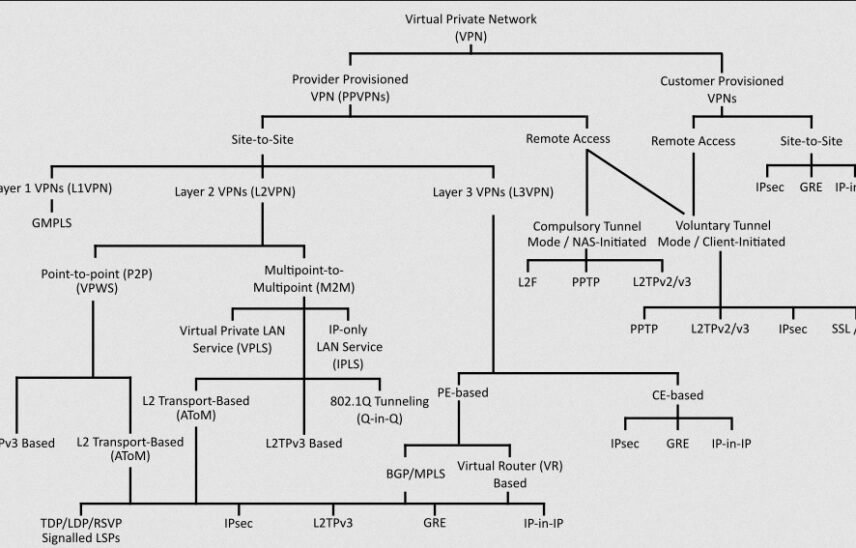
A virtual private network (VPN) is a means by which individuals can connect to the resources of an internal network, via the Internet, which is a relatively insecure network. VPN is accomplished by creating a tunnel or encapsulating an entire packet within another packet and sending it over a network. The data tunneling is helpful in cases where it is desirable to obscure the identity of the device originating the traffic.
The tunneling requires the use of three different sets of protocols: The passenger protocol i.e. the original data, such as IPX, NetBEUI, or IPv4 that is carried. An encapsulating protocol is also required, such as GRE, IPsec, L2F, PPTP, or L2TP, which wraps around the original data. There also needs to be a carrier protocol, the protocol used by the network over which the information is traveling (“How Virtual Private Networks Work”).
As an added security layer, the data is encrypted by utilization of the IPsec, or PPTP/MPPE, or L2TP/IPsec protocols. For secure VPNs, the technologies that the VPN Consortium recommends are IPsec with encryption, L2TP inside of IPsec, or SSL with encryption. For trusted VPNs, the technologies that VPNC supports are: MPLS with constrained distribution of routing information through BGP, or the transport of Layer 2 frames over MPLS.
Multi-protocol label switching (MPLS) is a packet forwarding technology which uses “labels” to make data forwarding decisions. A label is a four byte; fixed-length identifier, located between a Layer 2 and Layer 3 header, which is used to identify a Forwarding Equivalence Class (FEC). A FEC is a group of IP packets that are forwarded over the same path, with the same forwarding treatment (Fischer, 2007).
IPsec VPN
At present, the two most popular VPN technologies are the Internet Protocol Security (IPsec) based VPNs, which function primarily at the network layer and Secure Sockets Layer (SSL) VPNs, which function primarily at the application layer. For the most part, IPsec is the most secure option because, when properly implemented, it provides the C.I.A triad for our network traffic. However, they differ in the underlying technology used, the function they serve, as well as in the potential VPN security risks they present (Sastry, 2011).
Strengths and Weaknesses
One of IPsec VPN’s strengths is the two encryption modes used by it, tunnel mode which is the default mode, and transport mode. Tunnel mode is used between gateways, and the entire IP packet is encrypted by IPsec. Transport mode, which is used with an encapsulating protocol, is used to transport between a client and a server, and only encrypts the data part of the packet. Another IPsec VPN asset is its’ ability to provide an always-on connection between locations.
IPsec VPN operates at Layer 3 of the network stack, which renders it application-agnostic, as such, any IP based protocol could be tunneled through it. However, IPsec’s application-agnostic design is also its weakness, as it does not have the ability to restrict access to resources at a granular level. Once a tunnel is set up, remote users can typically access any corporate resource as if they were plugged directly into the corporate network. IPsec VPN also requires client VPN software to be installed, and special configuration is required to ensure IPsec works well with the NAT setup (Sastry, 2011).
L2TP / IPsec. Microsoft Windows does not natively support straight IPsec, so administrators setting up VPNs to support Windows clients often offer IPsec over L2TP connectivity. L2TP running under IPsec has a much smaller but significant deployment. (VPN Consortium, 2008) Nonetheless, by default, every Windows VPN connection attempts to negotiate L2TP over IPsec first, and then reverts back to PPTP. However, connections can be explicitly configured to use PPTP or L2TP only. For example, on Windows 7, you may open the VPN connection’s Properties panel, choose the Network tab, and pick either L2TP or PPTP under “Type of VPN.”
SSL VPN
SSL VPNs, which uses TCP port 443 for connections, were designed with the mobile workforce in mind. SSL has three basic capabilities that may be used independently or in combination to provide security to network-based communications. These capabilities are: authenticating a server to a client, encrypting communications between client and server, and authenticating a client to a server
An SSL VPN can be thought of as an application proxy, providing granular access to specific corporate resources that a remote user can access using his or her browser without the need to install a client. Also, SSL VPNs provide an enterprise the ability to control access at a granular level to a specified end-user population. Similarly, built-in logging and auditing capabilities provide SSL VPNs the ability to perform host security policy compliance checks on remote assets connecting to the enterprise.
PPTP VPN
Point-to-Point Tunneling Protocol (PPTP), which uses TCP port 1723 to establish a connection, is a VPN technology designed to aid VPN deployments. It exists in multiple implementations, which are vendor specific, such as Microsoft PPTP. However, the most commonly-used underlying mechanisms for authentication and encryption have been found highly vulnerable. Even after many attempts to fix issues in the PPTP security hole, it can be stated that PPTP still exhibit major vulnerabilities and are not state-of-the-art. The only relatively safe way of deploying PPTP would be by using Transport Layer Security (TLS), which requires the implementation of an entire PKI infrastructure (Enders, 2012).
Encapsulating Protocols
Though there are many VPN protocols and technology components available, this document has thus far focused on the IPsec, SSL, and PPTP methods of VPN deployment. In this section I will examine other protocols that are equally vital to VPN implementation.
Prominent Protocols
Generic Routing Encapsulation (GRE). GRE is atunneling protocol developed by Cisco that can encapsulate a diverse variety of protocol packet types inside IP tunnels, creating a virtual point-to-point link to routers at remote points over an IP network.
Layer 2 Tunneling Protocol (L2TP). The two primary components of L2TP are, “control messages” which establish, preserve and clear tunnels and calls, as well as assuring guaranteed delivery. There are also “data messages”, which encapsulate PPP frames being carried over the tunnel; however data packets are “not” re-transmitted, in the event of packet loss.
Additionally, L2TP connections provide secure access when used in conjunction with IPsec. L2TP is an extension of PPTP, and is a synergy of the best features of PPTP from Microsoft and L2F from Cisco Systems. Although L2TP acts like a Data Link Layer protocol in the OSI model, L2TP is in fact a Session Layer protocol, and uses the registered UDP port 1701.
L2TP is a permutation of an IP encapsulation protocol, the L2TP tunnel is created by encapsulating an L2TP frame inside a UDP packet. This in turn is encapsulated inside an IP packet. The source and destination addresses of this IP packet define the endpoints of the connection. Because the outer encapsulating protocol is IP, we are able to apply IPsec protocols to the composite IP packet. This protects the data that flows within the L2TP tunnel, and we can then apply an Authentication Header (AH), Encapsulated Security Payload (ESP), and IKE (IBM, 2012).
Alternative and Legacy Protocols
Crypto IP Encapsulation (CIPE). CIPE for the most part is an obsolete Linux VPN implementation. CIPE used encrypted IP packets that were encapsulated in datagram (UDP) packets. The packets were then transferred over IP, with port 7777 as its default port, via UDP packets through the CIPE virtual network device over a carrier network to the remote computer.
Layer 2 Forwarding Protocol (L2F). This protocol supports the creation of secure VPN networks over the Internet, though it does not provide encryption itself, instead it depends on the protocol being tunneled to provide privacy.
Internet Protocol over Internet Protocol (IPIP). IP-in-IP encapsulation consists of one IP being packet encapsulated inside another. IP-IP tunneling is supported by Linux and all BSD operating systems and through a proprietary implementation by Cisco (Robinson, 2002).
Encryption Protocols
Prominent Protocols
Internet Protocol Security (IPSEC). This protocol suite provides security services at the IP layer by enabling a system to select required security protocols, determine the algorithm(s) to use for the service(s), and put in place any cryptographic keys required to provide the requested services. IPsec supports network peer authentication, data origin authentication, and integrity, confidentiality, and replay protection. It is the Encapsulating Security Payload (ESP) protocol in IPsec that provides anti-replay, encryption, traffic control and optionally may provide connectionless integrity, and data origin authentication. Whereas, the IP Authentication Header (AH) provides: connectionless integrity, data origin authentication, and an optional anti-replay service.
Internet Key Exchange (IKE). IKE defines an automatic means of negotiation and authentication for IPsec security associations (SA). SA is a security policy defined for communication between two or more entities; the relationship between the entities is represented by a key. The IKE protocol ensures security for SA communication without the pre-configuration that would otherwise be required.
IKE is a hybrid protocol, and implements two protocols, Oakley and SKEME, within an ISAKMP TCP/IP based framework. ISAKMP specifies the basis for key exchange and authentication; the Oakley protocol specifies a sequence of key exchanges and their services, such as identity protection and authentication; and SKEME specifies the mode of key exchange. Although IKE is not required for IPsec configuration, it provides benefits: automatic negotiation and authentication; anti-replay services; (CA) support; and the ability to change encryption keys during an IPsec session (Rouse, 2009).
Secure Shell (SSH). SSH is a UNIX based protocol utilized for securing data communication, between two networked computers, via TCP Port 22. SSH was designed as an alternative to Telnet and other insecure remote communication protocols, which would send information in clear text.
Challenge Handshake Authentication Protocol (CHAP). CHAP authentication uses the concept of challenge and response, which means that the authenticator challenges the caller to prove its identity. The challenge includes a random number and a unique ID that is generated by the authenticator.
The caller must use the ID, random number, and its CHAP security credentials to generate the proper response (handshake) to send to the peer. CHAP security credentials include a CHAP user name and a CHAP “secret.” The CHAP secret is an arbitrary string that is known to both the caller and the peer before they negotiate a PPP link (Oracle, 2010).
Microsoft Point to Point Encryption Protocol (MPPE). The MPPE protocol encrypts data in PPP or PPTP VPN based connections, with 128-bit key, 56-bit key and 40-bit key encryption schemes being supported.
Conclusion
IPsec VPN should be utilized in situations where an always-on connection is required. In these instances, granular ACL should be augmented with a Network Access Control (NAC) system, which can ensure that only sanctioned remote nodes connect to the enterprise. Also, IPsec, being application- agnostic, can support a number of legacy protocols and applications with minimal effort.
This is not the scenario with SSL VPNs, which were designed around Web-based applications, and deal with this deficiency by installing a Java or ActiveX agent on the remote asset. Enterprises should utilize SSL VPNs primarily as an access method for the mobile workforce where granular access control, auditing and logging, and security policy enforcement are essential.
Finally, L2TP / IPsec and PPTP VPN still have a fairly significant market share, and the competent IA practitioner should be versed in their deployment and maintenance
References
Enders, R. (2012). How secure is a PPTP VPN in comparison with other types of VPNs. Retrieved from http://searchenterprisewan.techtarget.com/answer/How-secure-is-a-PPTP-VPN-in-comparison-with-other-types-of-VPNs
Fischer, T. (2007). MPLS Security Overview. Retrieved from http://www.irmplc.com/downloads/whitepapers/MPLS_Security_Overview.pdf
How Virtual Private Networks Work. Document ID: 14106. Retrieved from http://www.cisco.com/en/US/tech/tk583/tk372/technologies_tech_note09186a0080094865.shtml
Layer 2 Tunnel Protocol (L2TP). (2012). IBM. Retrieved from http://publib.boulder.ibm.com/infocenter/iseries/v5r4/index.jsp?topic=%2Frzaja%2Frzajal2tpprotocol.htm
System Administration Guide: Network Services. (2010). Oracle.Retrieved from http://docs.oracle.com/cd/E19082-01/819-1634/pppsvrconfig.reference-21/index.html
Robinson, H. Malware FAQ: Microsoft PPTP VPN. Retrieved from http://www.sans.org/security-resources/malwarefaq/pptp-vpn.php
Rouse, M. (2009). Internet Key Exchange (IKE). Retrieved from http://searchsecurity.techtarget.com/definition/Internet-Key-Exchange
Sastry, A. (2011). IPSec VPN vs. SSL VPN: Comparing respective VPN security risks. Retrieved from http://searchsecurity.techtarget.com/tip/IPSec-VPN-vs-SSL-VPN-Comparing-respective-VPN-security-risks
VPN Technologies: Definitions and Requirements. (2008). VPN Consortium. Retrieved from http://www.vpnc.org/vpn-technologies.html